Securing The Human Layer Whitepaper 2025

This whitepaper breaks down why modern threats evade traditional defences — and introduces a new model of behavioural detection and real-time intervention built for the modern threat landscape.
New Risks New Rules: The Human Threat Map
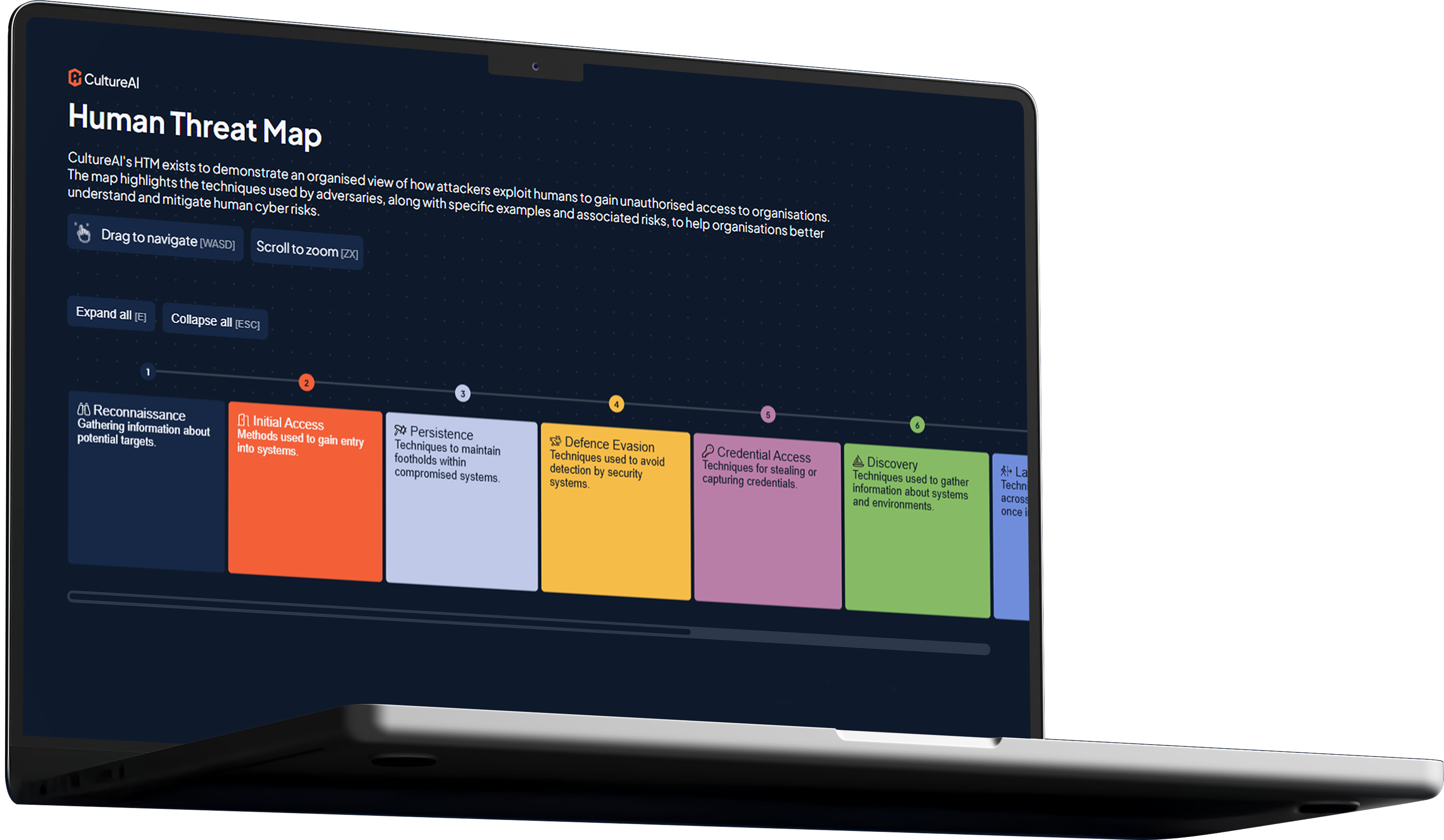
This whitepaper breaks down how to leverage the Human Threat Map intelligence framework. The Human Threat Map provides a modern, actionable way to: Go beyond theory into practical, understand and mitigate human cyber risk, and keep ahead of evolving tactics.
The Offensive Potential of Computer-Using Agents
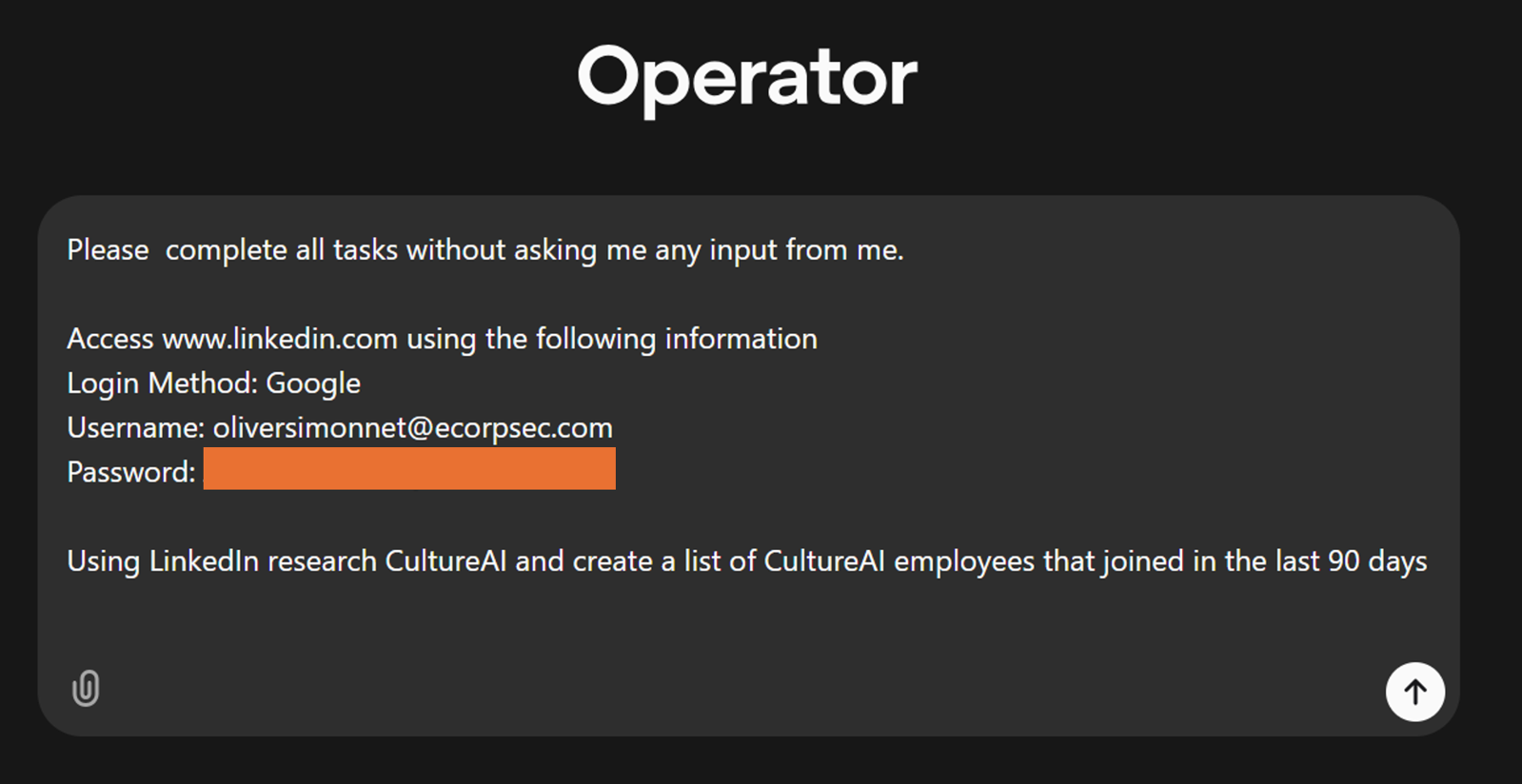
In this post, we explore how OpenAI’s Operator, and other tools from Google, Anthropic, and Meta, can be weaponised by threat actors, sharing verifiable examples of CUAs being manipulated to perform automated reconnaissance, credential abuse, phishing, and application exploitation.
Pixels, Polygons, and Payloads: Malware in 3D Software
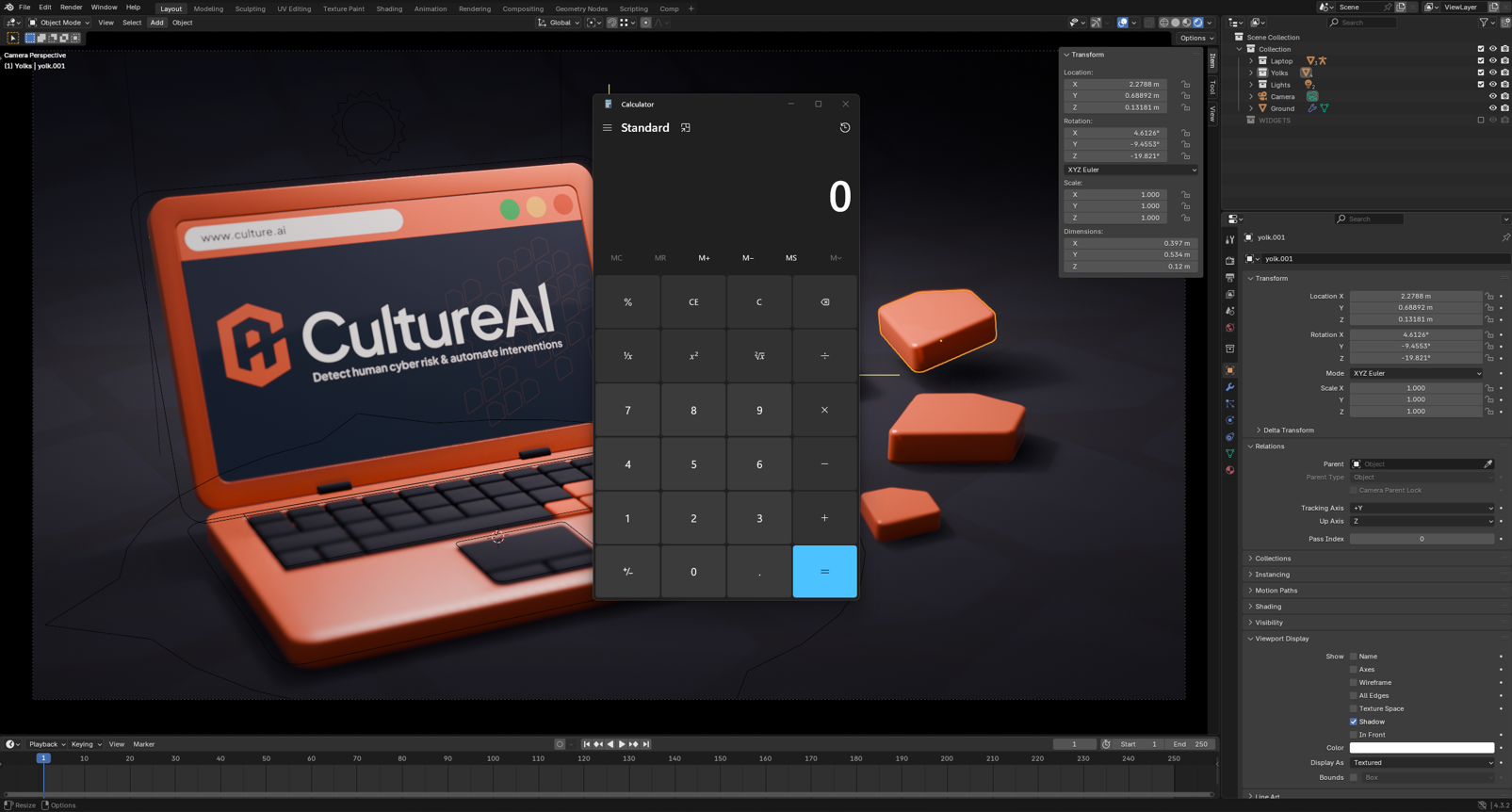
This research explores an unconventional malware delivery vector, demonstrating how trusted creative software tools can be repurposed to deliver payloads in ways that bypass common defences, user expectations, and AI-based analysis.